Seven security myths and their fatal effects
Cohesity, a leading provider of solutions for AI-supported data security, has conducted a survey of 1000 employees in Germany to investigate their knowledge of IT security. This revealed some dangerous myths that can have serious consequences for companies.
Even though the survey was conducted in Germany: Much of it is probably not entirely unknown in many Swiss companies either. However, some of these myths presuppose a certain naivety that is (hopefully) a thing of the past in most places:
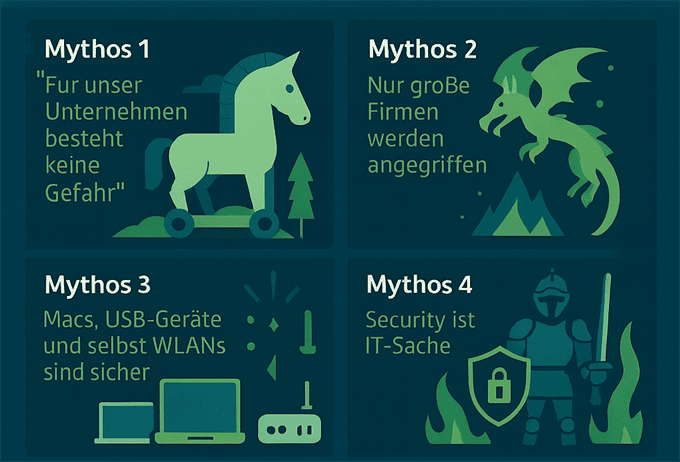
Myth 1: "There is no danger for our company"
According to the survey, German employees significantly underestimate the risks to their own company. For example, 53% do not believe that a ransomware attack could paralyze their company's business processes. 24% do not see any potential damage to their image and 18% do not see any impact on turnover. This is probably due to overconfidence in the company's security systems. However, these systems cannot block all attacks. For example, AI can be used to automatically create and send individual messages to employees based on generally available information in social media. These phishing attacks are becoming increasingly difficult to detect for both the victims and the defense systems.
Myth 2: "Only large companies are attacked"
15 percent of Germans assume that only large companies are attacked. However, several recent cases clearly show that medium-sized German companies are also regularly affected by ransomware attacks and can even become insolvent. This misjudgement of the threat situation shows that many employees still assume that cyber criminals are targeting specific companies. However, automated tools and AI have fundamentally changed the situation. Today, hackers scan the entire internet for potential security gaps and indiscriminately attack any company that has an open vulnerability.
Myth 3: "Macs, USB devices and even WLANs are secure"
A similarly outdated level of knowledge is evident in the assessment of device security. Only 36 percent of Germans believe that Mac devices are vulnerable to attack. However, their higher level of security compared to Windows devices in the 1980s and 1990s was due to the fact that they were closed systems that were not connected to the internet. The situation is not much better for other devices: only 41% consider cell phones to be at risk, 49% USB devices and 52% each for collaboration platforms and WiFi. Even for PCs and websites, the figures remain below two thirds, although all of these systems are used for attacks in practice.
Myth 4: "Security is an IT matter"
One reason for this attitude is a lack of sense of responsibility: Most respondents see the IT (39 percent) or cybersecurity team (34 percent) as the main people responsible for protecting the company. Only 10 percent are aware that everyone in the company is equally responsible for security. After all, even a careless click on a link can cause devastating damage to the company. Even the most modern security systems cannot detect 100 percent of all threats.
Myth 5: "Companies should pay a ransom"
After a ransomware attack, many employees see paying the ransom demanded as the quickest way to recover their data. 13 percent even believe that paying the demand will definitely get the data back intact. In reality, however, there is no guarantee that cyber criminals will keep their promises. And even if they offer decryption, the affected companies often do not get all their data back undamaged.
Myth 6: "Patches are enough"
Timely updates are an important tool to protect against attacks. However, they also lull employees into a false sense of security. For example, 80 percent believe that their own company has sufficient security measures in place to prevent dangerous cyber attacks. However, patches or even existing firewalls and intrusion prevention solutions are not enough. This is because they are often unable to fend off zero-day attacks that exploit unknown or recently discovered vulnerabilities for which no patches or virus signatures are yet available. In addition, the risk of new and constantly changing attacks by AI systems is increasing significantly. Therefore, solutions for anomaly detection, multi-factor authentication and role-based access controls must also be used.
Myth 7: "Backups restore all data"
Employees in Germany are overconfident when it comes to recovery. For example, 78% are confident that their company will be able to recover from a dangerous cyberattack. Backups can play an important role here, but only if they have not also been attacked and modified. Cyber criminals have recognized this and often encrypt the backup data first so that the victim cannot simply restore it. Companies therefore need immutable backups, a secure cyber vault and a clean room containing the most important applications, data and systems for recovery.
Source: Cohesity