An alternative offers a passwordless MFA
The login with username and password is still standard. But this procedure has many disadvantages and companies are looking for alternatives. One possibility is the passwordless MFA.
Although more than 80 percent of all security incidents are related to stolen, spied-out or too weak passwords, most companies still rely on the classic login procedure with user name and password. But it's not just the poor security that speaks against this access method. Companies are also looking for alternatives to password-based logon because of the negative impact on employee productivity and the considerable administrative costs. Such alternatives already exist, as smart cards and public key cryptography enable secure authentication. Meanwhile, a smartphone can also be used as a smartcard, which greatly simplifies the introduction of technology for passwordless MFA.
Authentication specialist Hypr gives tips on how to introduce a true passwordless login and shows what companies should look out for:
1. inventory I: Where are passwords most annoying?
When implementing a passwordless authentication solution, organizations should first analyze in which areas the negative impact of a password-based login is greatest:
- Where are they most annoying for the user?
- Where do they cause the most stress in the IT department?
- Where are they worst for productivity and most dangerous for safety?
- Which are the most critical systems in the company?
Inventory II: Which solutions are already in use?
To minimize the use of insecure passwords and circumvent the negative impact of password-based logins on employee productivity, organizations are already using tools such as password managers or single sign-on (SSO) procedures - or a combination of both.
However, these methods do not offer a much higher level of security. Finally, these techniques are based on passwords stored in a central database, which is potentially vulnerable to cyberattacks. In addition, many passwords are merely hidden by one, creating a single point of failure that carries significant potential for damage.
3. check multi-factor authentication (MFA)
When implementing an MFA solution, it is important to distinguish between perceived and true passwordlessness: To improve the security of password-based login methods, many organizations use multiple factors to authenticate a user. Most multi-factor authentication solutions rely on passwords and shared secrets - that is, an additional password increases the security of the login. Now that enterprises are increasingly using different cloud services, they face the dilemma of having to manage multiple identity platforms. And end users are faced with numerous multi-factor login methods that are becoming increasingly complex and inconsistent, negatively impacting their productivity.
It is true that a conventional MFA offers a higher level of protection than logging in with just a user name and password. But shared secrets are still used, which are stored centrally in a database and are vulnerable to a hacker attack.
4. caution: passwordless is not equal to passwordless
When implementing passwordless authentication, organizations should ensure that the solution offers true passwordless multi-factor authentication. Unlike password-based MFA techniques, passwords are replaced with secure cryptographic asymmetric key pairs, so hacking is only conceivable on individual devices, not on a credential database with numerous credentials.
In addition, passwordless MFA relieves the IT help desk by significantly minimizing the cost of managing credentials, such as in the event of a password reset.
5. real passwordless MFA already at the desktop increases security
An important criterion for the introduction of a passwordless MFA solution is that it can already be used when logging on to the desktop. This means that protection against attacks is implemented at the earliest possible stage and not just when the user is already in the network. It is of great importance that the solution also works offline, so that users are protected at all times and can, for example, access their laptop even without a network connection. This is the only way to ensure that they do not have to revert to username and password as a fallback and that this insecure login variant can be ruled out.
6. evaluate integration, compatibility and sustainability
A passwordless MFA solution that is flexible, integrates with existing systems such as identity access management solutions and cloud services, and supports legacy applications is recommended.
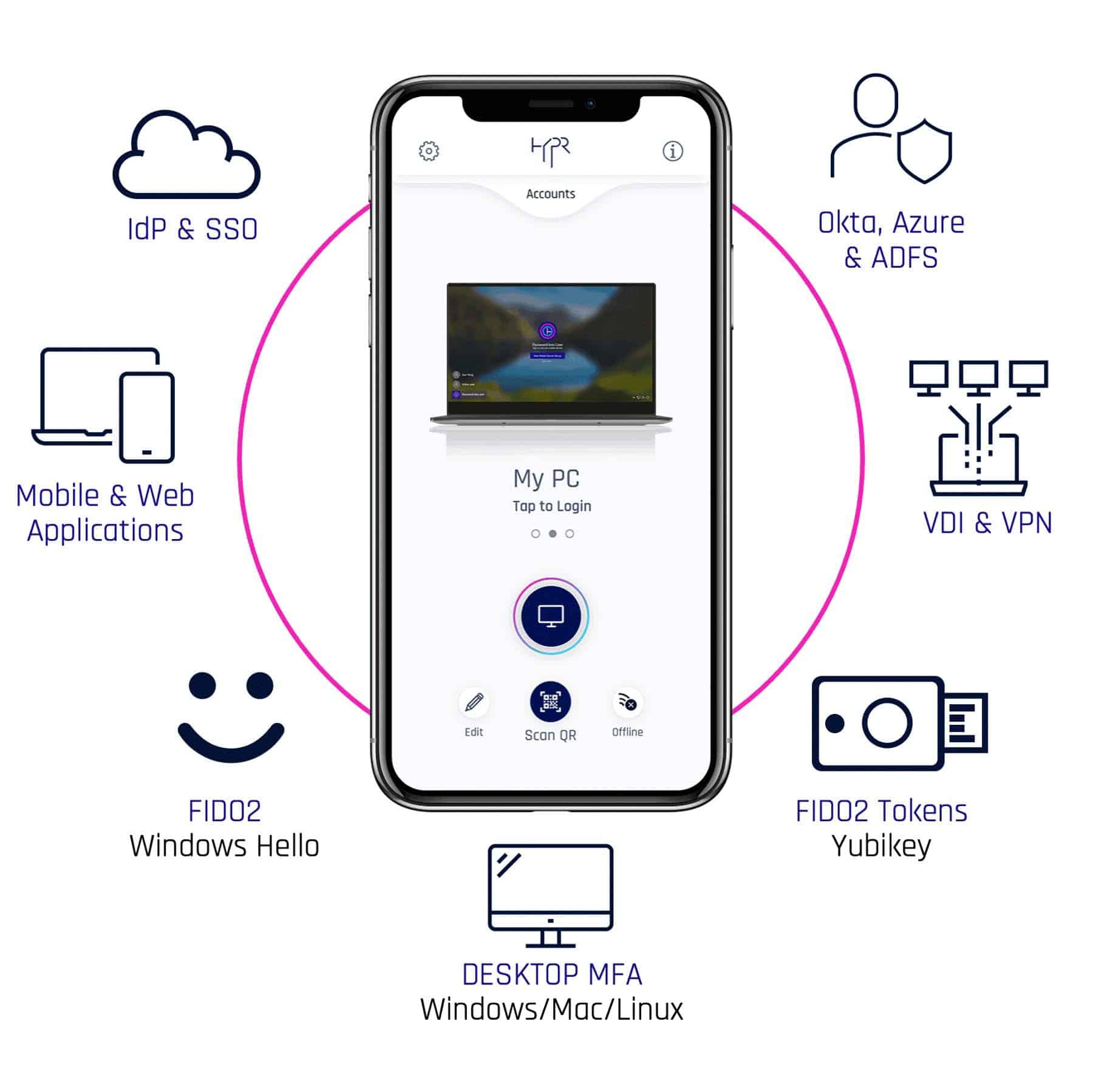
It should also be compatible with other true passwordless technologies, such as security tokens like smart cards and FIDO sticks, and also support the solutions already integrated in various laptops, such as Windows Hello and Touch ID. Use for mobile and web applications, VDI and VPN environments, remote desktop connections, and support for security standards such as FIDO2 should be a given. Optimally, such a solution also works with future applications and services thanks to compatibility with standards.
7. more user comfort thanks to access via smartphone
An optimal passwordless MFA also supports modern devices such as smartphones and provides an efficient and consistent user experience. Thus, the login can be initiated on the smartphone (factor: ownership) and authenticated by biometrics (factor: inherence) or a PIN (factor: knowledge). It is important that the open industry standard for two-factor authentication defined by the FIDO Alliance is supported. Only then can the smartphone also become a smartcard.
"If a company uses or introduces a passwordless authentication solution, it should carefully check whether it is a real or just a user-oriented passwordless solution," explains Jochen Koehler from Hypr. "It is also clear that above all, passwordless multi-factor authentication offers the highest possible security - and very importantly: already at the operating system login. So you don't let the hacker into the house first and then forbid him access to the bedroom, but you already fend him off at the front door."
Source: Hypr
Other topics:









