Ransomware: Almost every second company pays - often after negotiation
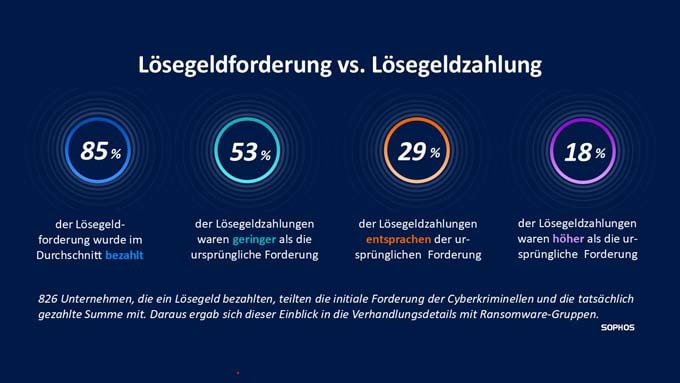
The IT security service provider Sophos has published its annual "State of Ransomware 2025" report. The survey of 3,400 IT and cyber security managers in 17 countries reveals one particularly striking result: Almost 50 percent of the companies attacked paid a ransom to the cyber criminals to recover their data. What is even more interesting is that over half of these companies apparently negotiated with the cybercriminals and paid a lower amount than the original demand.
According to the recently published "State of Ransomware 2025" report by Sophos, almost half of the companies surveyed have already paid a ransom. The average amount of the ransom is around 1 million US dollars (€ 869,591). What is new is that 53 percent of companies have negotiated a lower amount than the original demand. Nevertheless, this is the second-highest rate of payment for ransom demands in six years (the highest level was 56% in the 2024 report). In the latest report, the willingness of victims in Germany (63%) and Switzerland (54%) to pay was above average.
Companies negotiate ransom payments
Despite the high percentage of companies that paid the ransom, more than half (53%) paid less than originally demanded by the cybercriminals. The affected companies in Germany (47%) and especially in Switzerland (65%) also showed their negotiating skills with the cybercriminals and also paid lower amounts than originally demanded.
The average ransom demand fell by a third between the reports of the last two years from an international perspective. At the same time, the average ransom payment fell by 50 percent. This development shows that companies are increasingly successful in minimizing the impact of ransomware attacks.
Ransom demands and payments vary greatly by country
Worldwide, the average ransom demand (median) was 1,324,439 million dollars (€ 1,159,905). At country level, however, the median demand amounts vary greatly; here are some examples:
- 600 thousand dollars (€ 525 thousand) in Germany
- 643 thousand dollars (€ 563 thousand) in France
- 4.12 million dollars (€ 3.61 million) in Italy
- 5.37 million dollars (€ 4.7 million) in the UK
- 2.0 million dollars (€ 1.75 million) in the USA
The ransom sums paid regionally in the sample countries amount to:
- 412 thousand dollars (€ 361 thousand) in Germany
- 232 thousand dollars (€ 203 thousand) in France
- 2.06 million dollars (€ 1.8 million) in Italy
- 5.20 million dollars (€ 4.55 million) in the UK
- 1.50 million dollars (€ 1.53 million) in the USA
Vulnerabilities and scarcity of resources are significant risk factors
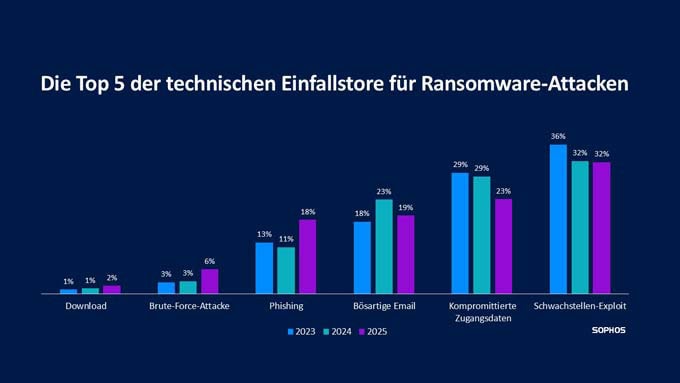
For the third time in a row, exploited vulnerabilities were the most common technical cause of attacks. 40% of all ransomware victims surveyed stated that the attackers exploited a vulnerability they were unaware of. In Germany and Switzerland, this situation is even worse at 45% and 42% respectively. This illustrates the ongoing difficulties companies have in recognizing and securing their attack surface.
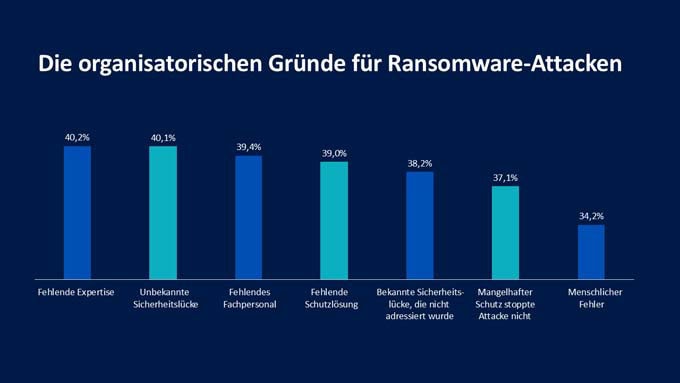
63% of the companies surveyed worldwide confirmed that resource problems were a factor in their falling victim to the attack. Companies in Germany (67%) and Switzerland (72%) are even above the international average in this respect. Globally, a lack of specialist knowledge was cited as the most important operational cause in companies with more than 3,000 employees. Companies with 251 to 500 employees were most likely to struggle with a lack of human resources or capacity.
Internal and external resources are crucial
"In 2025, most organizations see the risk of falling victim to a ransomware attack as a part of everyday business. The good news is that thanks to this increased awareness, many organizations are equipping themselves with additional resources to limit the damage. This includes hiring incident response specialists who can not only reduce ransomware payments, but also speed up recovery from an attack and even stop attacks in progress," said Chester Wisniewski, Field CISO at Sophos. "A real game changer in the fight against ransomware is focusing on the root causes of the attack potential. These include, above all, exploited vulnerabilities, a lack of transparency regarding the attack surface in the company and too few resources. We are seeing that more and more companies are realizing that they need help and are turning to MDR (Managed Detection and Response) services to defend themselves. This cybersecurity service, in conjunction with proactive security strategies such as multi-factor authentication and patching, makes a decisive contribution to preventing ransomware in the first place."
Best practices for effective protection against ransomware and other cyberattacks:
- Taking action to eliminate common technical and operational causes of attacks, such as exploited vulnerabilities. Tools such as Sophos Managed Risk can help companies to determine their risk profile and minimize their risk in a targeted manner.
- Ensure that all endpoint devices (including servers) are equipped with special anti-ransomware protection.
- Provision and testing of an incident response plan. Good backups and regular practicing of data recovery play an important role in this.
- 24/7 monitoring and detection. If companies do not have the necessary internal resources, trusted Managed Detection and Response (MDR) providers can help to meet these requirements.
Source: Sophos